Cybersecurity solution for industrial control systems (InteRSePT)

Distributors :
Detects and responds to cyber incidents on control systems
Targeted cyberattacks on control signals are detected using Mitsubishi Heavy Industries' unique “behavior detection” technology, developed from extensive experience accumulated in its engineering of control systems for critical infrastructure and operational technology sites. Furthermore, InteRSePT® in collaboration with Nozomi Networks combines its strength with the power of Nozomi Networks Guardian™ to deliver higher visibility and detection by asset, communication, and protocol monitoring.
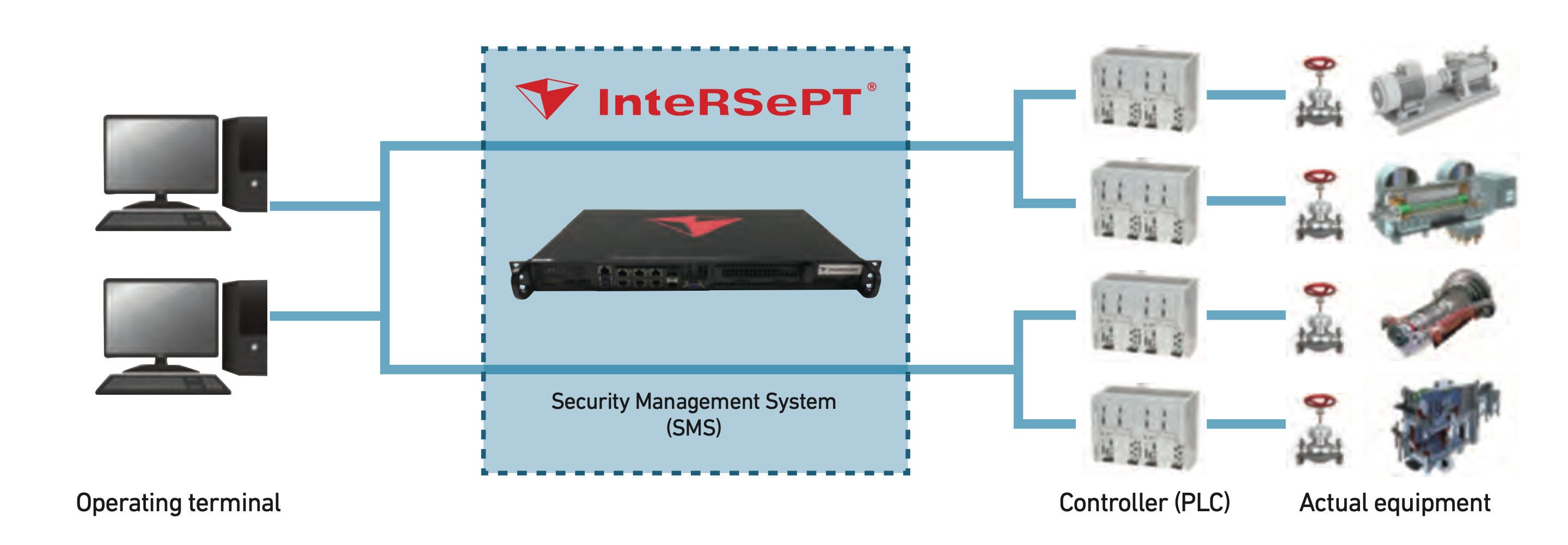
The Security Management System (SMS) can be applied without requiring modifications to target systems and monitors the systems without interruption or deterioration in performance.
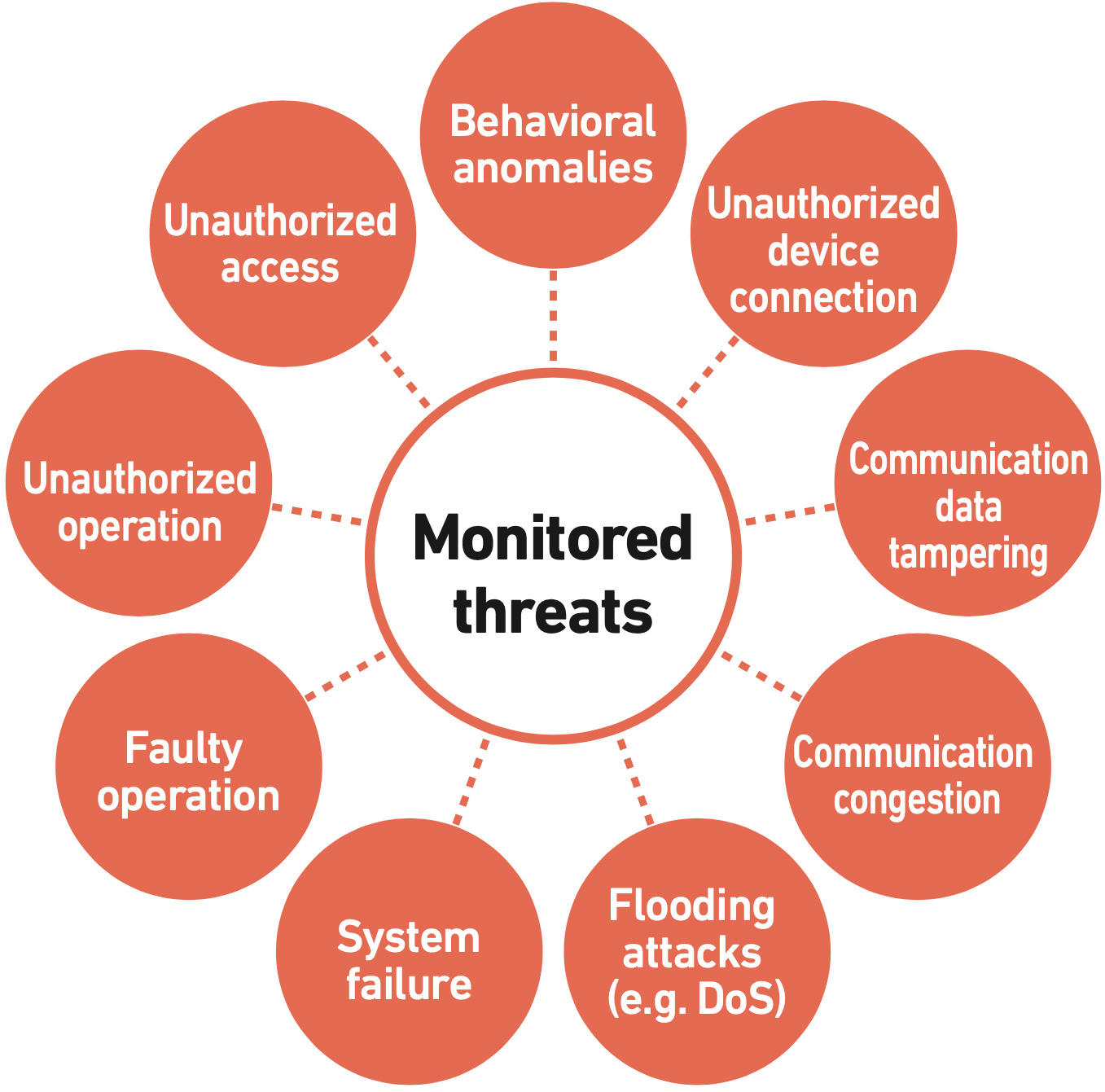
InteRSePT® advantages
- Protection even from advanced persistent threats that imitate the behavior of control systems
- Monitoring of the behavior of devices, processes, and communications
- Advanced behavior detection rules designed from characteristics and operations of the monitored system
- Tailored technical support of detection rules from MHI Group
- Safe, passive detection that does not affect the control system
- Visualization and detailed monitoring of assets and network status
- Detection of intrusions, unauthorized behavior, incidents, device failures, and other anonymous activities
- Intuitive dashboard for improved visibility of operation status and alerts
- Real-time interception of unauthorized control signals
(Optional function with Real-time Network Monitoring System)
Key functions of InteRSePT®

Basic system configuration
Functions
| Behavior detection |
Collects and analyzes commands and sensor values in 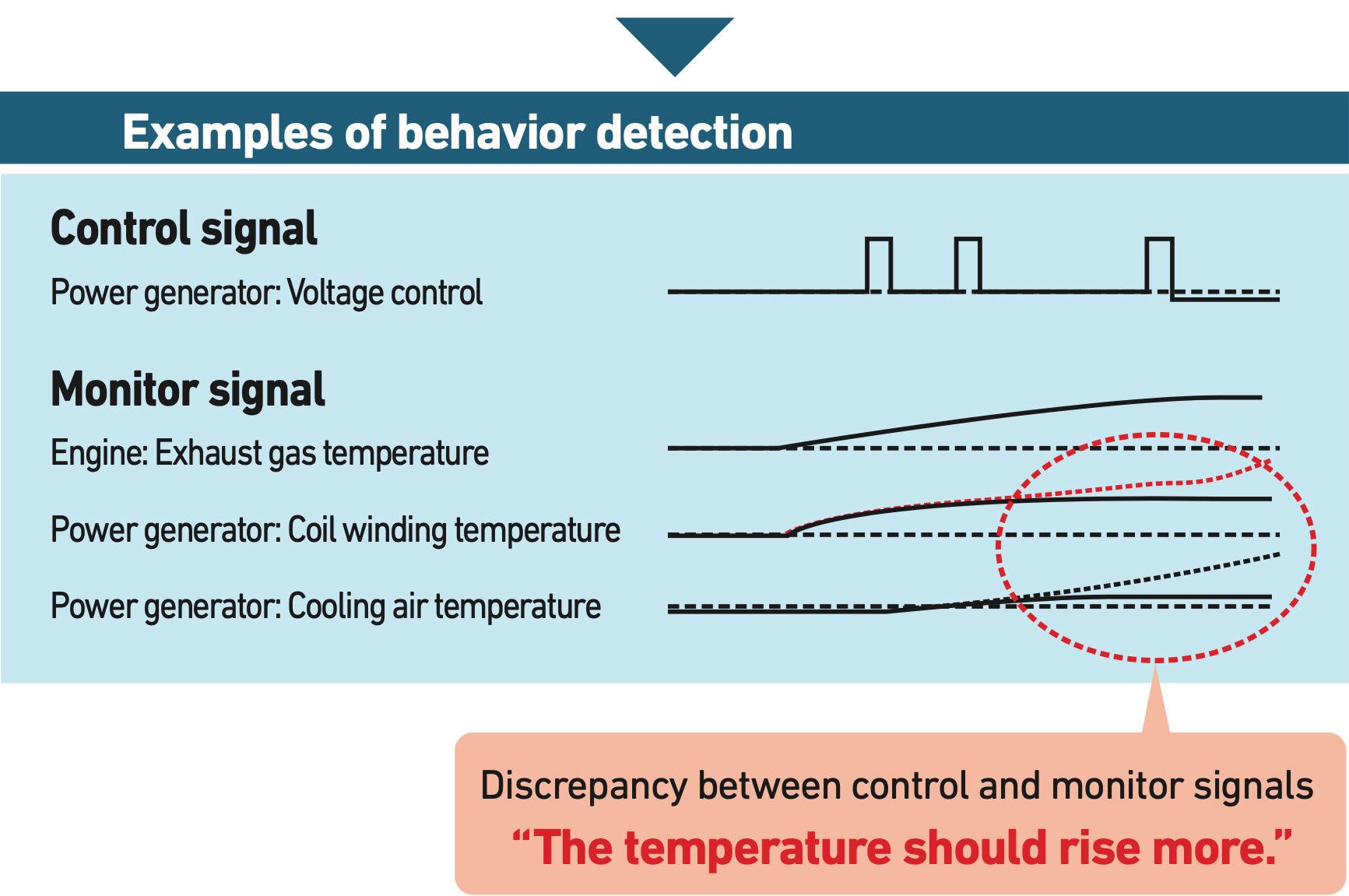
|
|---|---|
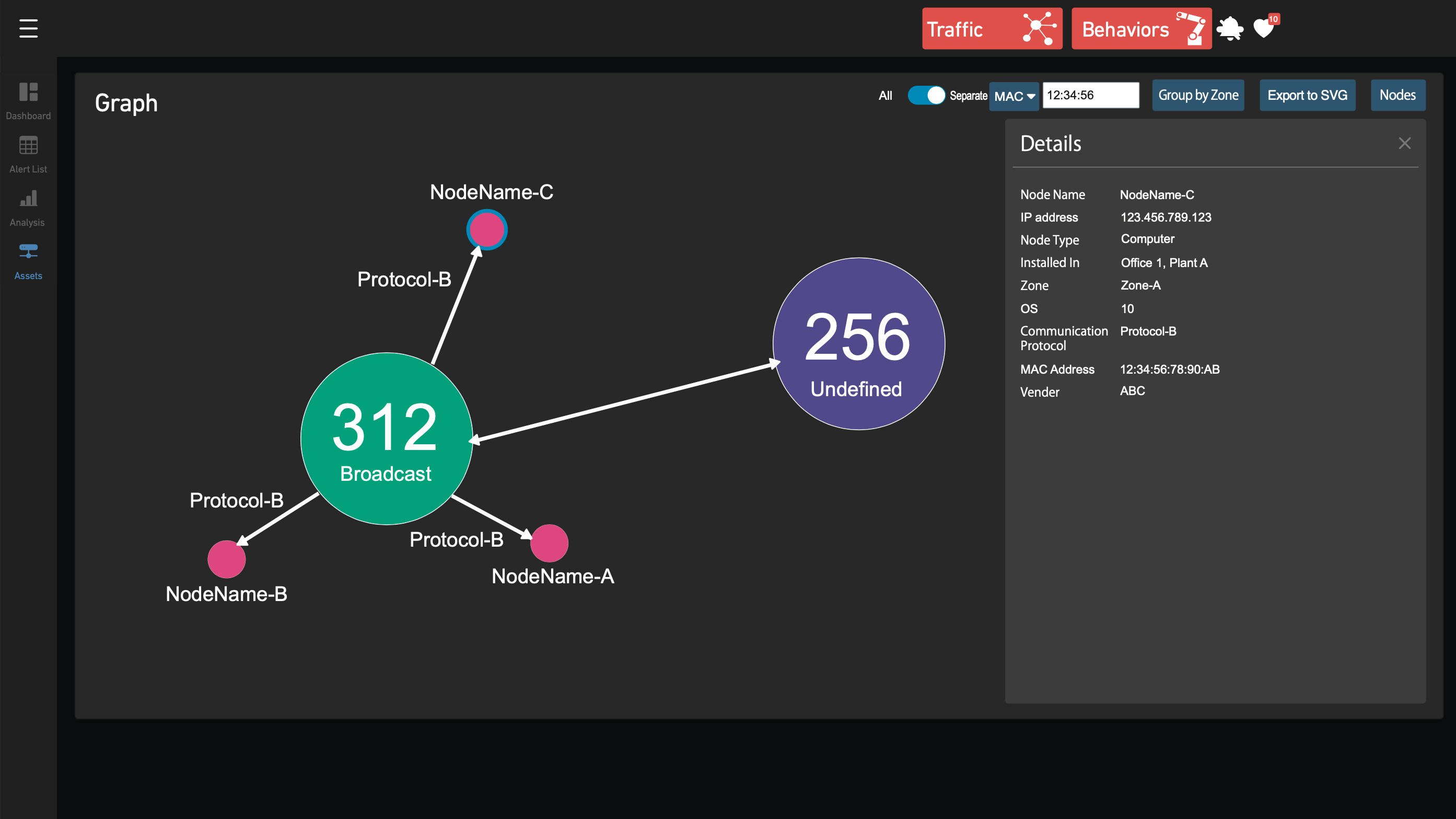
| Asset monitoring |
Visualizes the devices connected to the network. |
| Unauthorized device detection |
Detects the connection of unauthorized devices. |
| Unauthorized communication detection |
Detects unauthorized communication. |
| Attack detection | Detects attack patterns (DoS, port scanning, man-in-the-middle attacks, unauthorized operations, etc.). |
| Network monitoring |
Visualizes network communication status, protocols, and other profiles. |
| Device information display |
Presents information about network devices. |
| Alert list | Issues warnings of detected anomalies and visualizes the current response status. |
| Alert trend | Displays a graph of sensor values related to alerts. |
| Alert analysis | Gives analysis of alerts. |
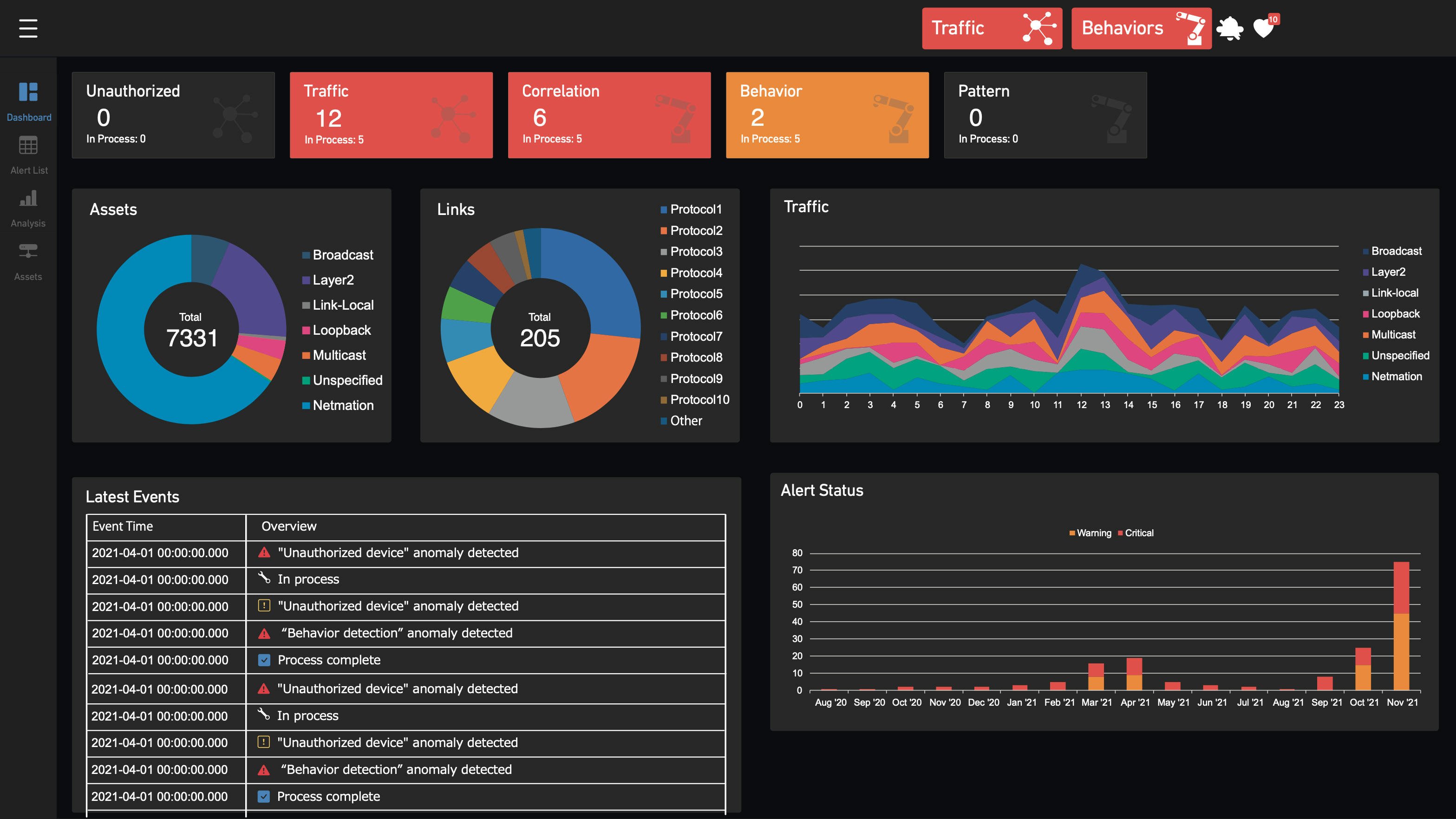
Dashboard
With a dashboard that visualizes network topology, assets, communication status, alerts, and more, InteRSePT® gives you a clear picture of your monitoring status.